How my Alexa voice assistant’s bedtime routine settles my kids down for an easy bedtime, every single night.

As parents of young children, we dream of quick and pain-free bedtimes with no tantrums, tears, or bargaining. Our kids, on the other hand, often see bedtime as playtime in a different room with the lights turned down.
To combat this, my wife and I have a strict bedtime routine to ensure our little ones fall asleep happily with the least resistance possible. Our beloved Alexa is a critical member of our team. This is how it works.
Our Amazing Alexa Kids Bedtime Routine
After dinner, it’s time for a bath with some playtime followed by a wash and wind-down time. Then it’s pyjamas on, hair and teeth brushed, and into bed with a bottle of milk and a story. Once the story is done, Alexa takes over.
“Alexa, night night”
“Night night, sweetheart”, Alexa replies. The delicate sound of Baby Mine from Dumbo played soothingly on a xylophone fills the room with an audible warmth.
Within a few minutes, my little one is asleep.
Like Pavlov’s dogs, we’ve conditioned my eldest to associate going to sleep with our chosen Spotify playlist. My youngest daughter is only 7 weeks old and we’ve already started planting that same mental trigger in her head.
We could do all of this without Alexa, but having a voice assistant that kicks off the routine on a spoken command makes consistency so easy to maintain it would be more difficult to not be consistent.
Setting Up The Perfect Kids Bedtime Alexa Routine
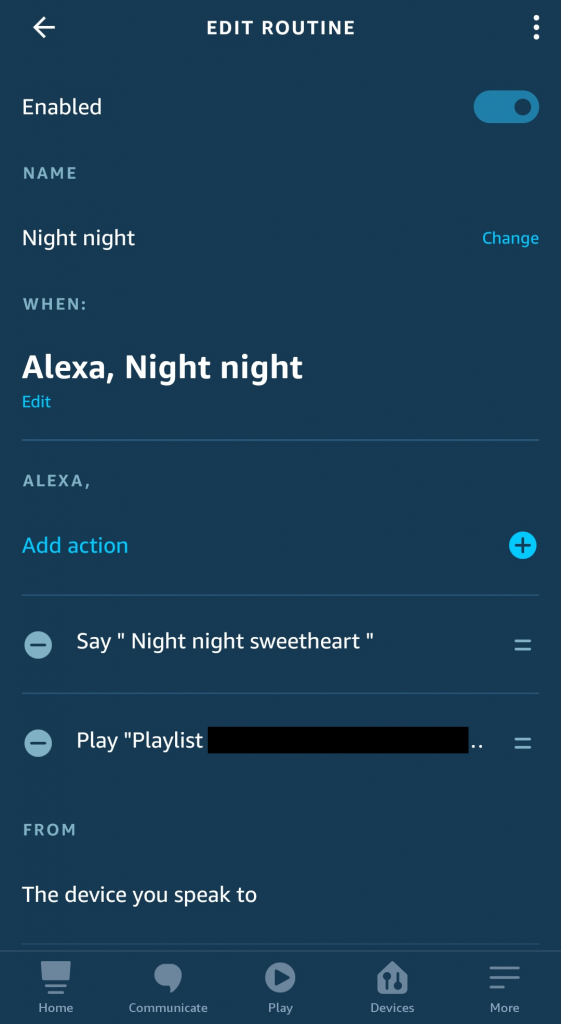
- From the Alexa app, go to More > Routines, then create a new routine by clicking on the + icon in the top right corner.
- Give your new routine a suitable name. I simply call mine ‘Night night’.
- Pick your welcome phrase. When I say “Alexa, Night Night”
- Add your actions. Mine are:
- Alexa says, “Night night, sweetheart”
- Play my kids’ bedtime playlist on Spotify
- From the device that I’ve spoken to.
The Spotify playlist is a custom playlist I’ve created that is simply the album “Disney Lullabies” from the artist “Rockabye Lullaby”, released in 2011. I created a playlist as, for some reason, Alexa struggles to find the album when referenced directly. Instead, the uniquely named playlist ensures that it plays the correct album every time. The last thing I want when putting my kids to sleep is unexpected death metal.
Consistency at Bedtime is Critical
Having a consistent bedtime routine is the most important element of this. The Alexa technology is a nice-to-have, hands-free, luxury that means I don’t need to get up and disturb my soon-to-be-sleeping child in order to start the music. But it isn’t Alexa that actually makes them sleep.
Doing the same thing every night establishes an automatic behavioural response from the kids which helps us to achieve what we want. Familiarity over novelty.
Recently, while my eldest was acting up at bedtime, I dropped the “Alexa, night night” bomb and as soon as the music came on she climbed straight into bed and lay down without any further encouragement. I was stunned. While I hoped it would calm her down, I didn’t think the effect would have been so instantaneous and overwhelming. I would never have thought going from tantrum to tucked up tight so quickly was possible.
Alexa routines are a great way to automate consistency in your life. Don’t get me wrong, bedtimes haven’t always been this easy, but the effort we’ve put into establishing this routine has been well worth it. Now if only Alexa could do laundry…