Nmap is one of my go-to tools for network discovery and asset detection and Nmap OS detection is a quick and powerful way to determine what operating system a remote device is running.
Basic Nmap OS Detection
The most basic version of the Nmap command for Operating System detection is:
nmap -O <target>
While it’s not always easy to tell on screen, the flag on this command is -O for Operating System. Not to be confused with the lowercase -o which is used for Output, or the number Zero.
<target> should be switched with whatever you’re trying to scan. That could be either the hostname of the target such as scanme.nmap.org, or the IP address of the target such as 45.33.32.156.
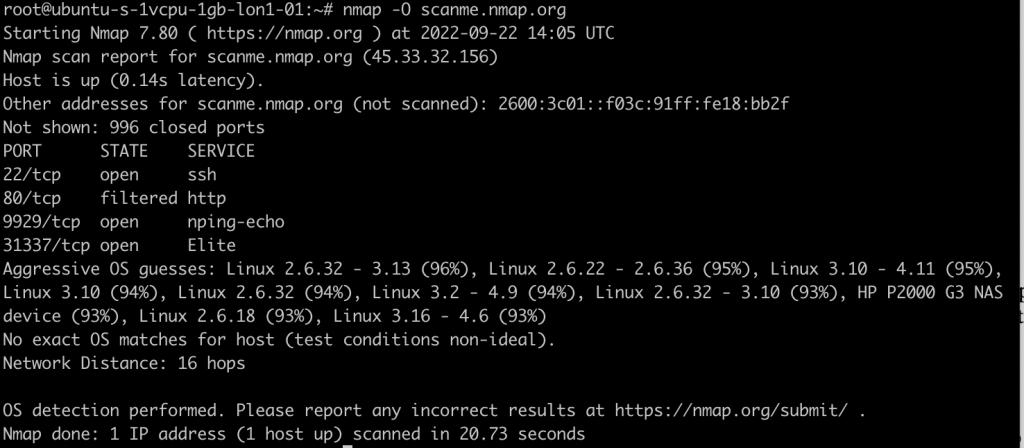
Nmap os detection confidence levels
As you’ll see in the above scan screenshot, Nmap doesn’t always know for sure the exact operating system in use by a target device. In those cases, it makes predictions with confidence levels shown as percentages, e.g. Linux 2.6.32 – 3.13 (96%). Because of how Nmap os detection works unless the device replies with the exact OS and version number this can be the best you can get. The more information Nmap can gather, the more accurate the prediction will be.
False positive reduction with Nmap os detection
Because of how os detection works, sometimes a basic -O scan will have many different high-confidence guesses and it’s possible that none of them are completely accurate. A good trick to remove the noise and confirm the underlying operating system is to run an aggressive Nmap scan with both OS and application version detection:
nmap -A -T4 <target>
The -A flag includes -O for Operating System detection and upgrades it to Application version detection. The -T4 flag is for aggressive timing (T0 to T5, least to most aggressive). Application version detection can take quite a while with default timing so T4 helps to speed things up a little. It also makes it more obvious that you’re scanning so if stealth is important to you, keep it at T0 or T1.
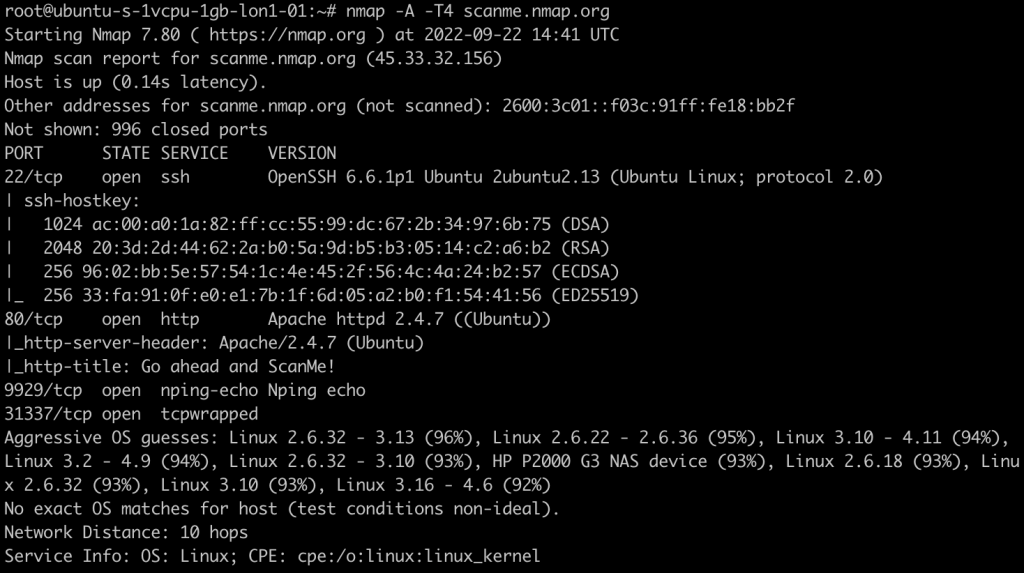
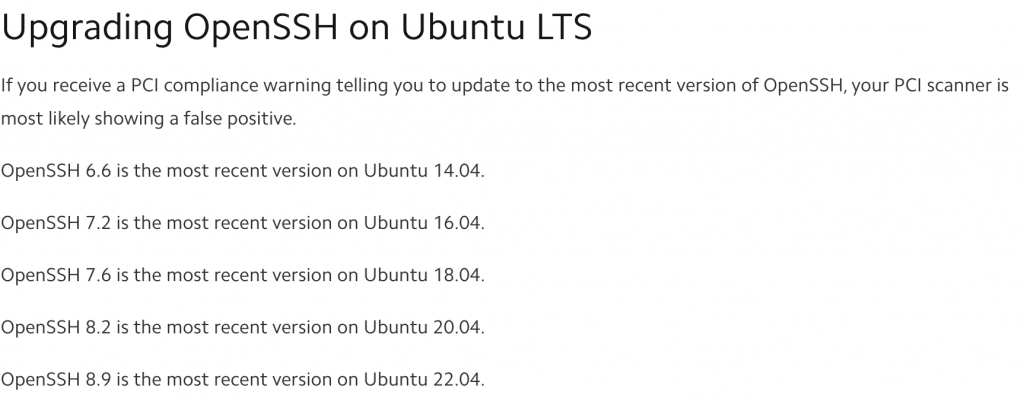
The screenshot above shows the result of an -A -T4 scan against the same target as before. Unfortunately, the Aggressive OS guesses are still the same. Thankfully, in this example, we can see that the OpenSSH version states 2ubuntu2.13 which indicates that the server is running on Ubuntu operating system. A quick Google for “ubuntu OpenSSH versions” indicates that the server is most likely to be running on ubuntu 14.04, assuming the server is fully patched.
Basic firewall evasion for Nmap os detection scans
Some servers and firewalls are configured to block ICMP ping scans and Nmap uses ping to test if a server is alive before trying to port scan it. To bypass this simply disable the default ping check by using the command:
nmap -O -Pn <target>
The -Pn flag disables the ping check: no Ping aka Ping:no. Nmap then assumes that the host is up and performs a port scan and os detection scan. This can be combined with other scan types such as:
nmap -Pn -A -T4 <target>
The result is a scan that skips ping checks, tests for operating system versions and application versions, and runs aggressively with probing messages sent rapidly for faster results.
These scans are easily detected and blocked by modern, advanced, and well-configured firewalls. Fortunately, most devices aren’t protected by modern, advanced firewalls. Those that are, more often than not, are poorly configured.
Advanced firewall evasion
The reality is, if a host is detecting and blocking anything above the most simple and basic Nmap scans then your attempts at os detection are going to fail more often than not.
In these situations, you’ll need to consider more passive approaches such as Open Source Intelligence (OSINT) to find the information you need. This could include looking at job openings to identify the tech stack used within a company, looking for the technologies deployed to a device in case they are OS exclusive (e.g. Microsoft IIS only runs on Windows), and so on.
How does Nmap OS detection work?
Nmap OS detection works by using a technique called TCP/IP Stack Fingerprinting. While TCP/IP is a mature and well document standard, different operating systems have implemented these protocols in slightly different ways. They are still compliant with the specification and can still talk to each other without problems, but the subtle differences in how each operating system handles ambiguities in the specification can be used to identify the underlying operating system of a network-connected device.
The Nmap developers maintain a thorough and comprehensive database of operating system and application version signatures which are installed with every installation of Nmap. It’s important to keep Nmap up to date in order to download the most recent signature updates for new operating systems and applications.
The Nmap official book explains the inner workings in detail, but in a nutshell:
Nmap OS fingerprinting works by sending up to 16 TCP, UDP, and ICMP probes to known open and closed ports of the target machine. These probes are specially designed to exploit various ambiguities in the standard protocol RFCs. Then Nmap listens for responses. Dozens of attributes in those responses are analyzed and combined to generate a fingerprint.
https://nmap.org/book/osdetect-methods.html