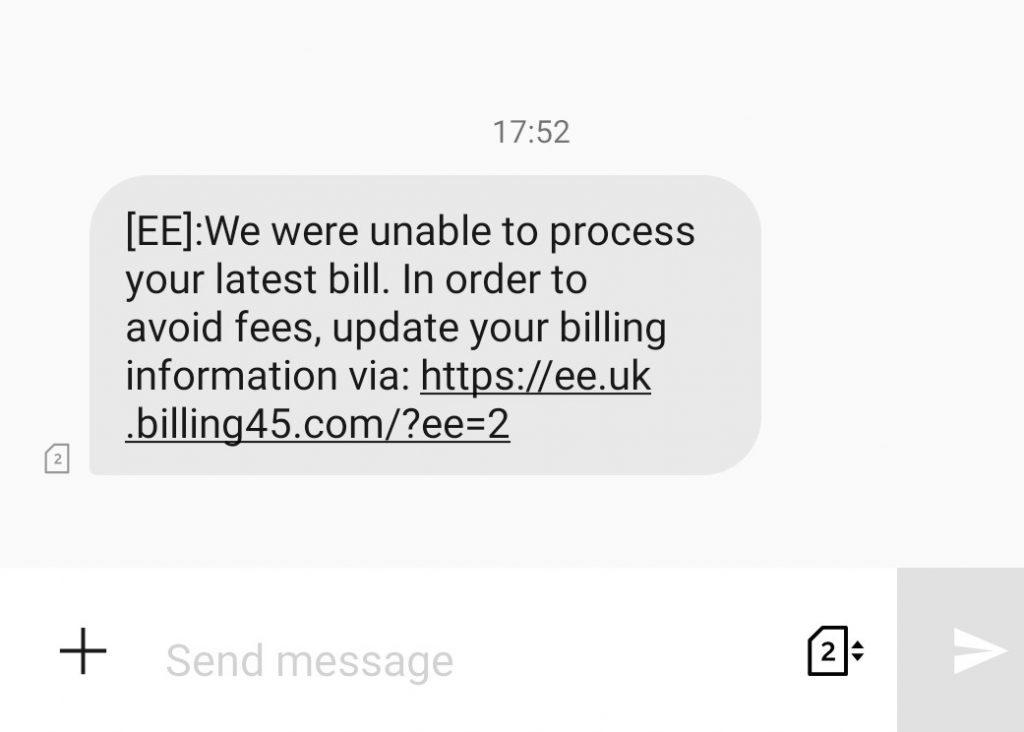
Over 60 percent of people who are phished by email are phished on mobile devices. This is why it happens and what you can do about it.

Why Mobile Devices are More Prone to Phishing
I’ve sent a lot of phishing emails. All with good intentions I must add. While reviewing the results, one of the most surprising things that I discovered was that the majority of people who fall for phishing tests (and therefore real phishing attacks) are using mobile devices. In my experience, 60% of those who are successfully deceived are victims of mobile phishing.
These are my conclusions as to why this is true and recommendations on what we can do to help people stay safe online.
[Read more…] about Why More Than Half of Email Phishing Leaks Happen on Mobile Devices