Over 60 percent of people who are phished by email are phished on mobile devices. This is why it happens and what you can do about it.

Why Mobile Devices are More Prone to Phishing
I’ve sent a lot of phishing emails. All with good intentions I must add. While reviewing the results, one of the most surprising things that I discovered was that the majority of people who fall for phishing tests (and therefore real phishing attacks) are using mobile devices. In my experience, 60% of those who are successfully deceived are victims of mobile phishing.
These are my conclusions as to why this is true and recommendations on what we can do to help people stay safe online.
Mobile Devices Don’t Get Our Full Attention
People using mobile devices are often busy. When we sit down at a computer we’re there to use it as the primary task. When we’re using mobile devices however, we’re often using it between doing primary tasks. Reading email on a mobile device is a distraction from whatever boring things are going on at that time. Stuck on a train? Waiting for a taxi or Uber? Left alone at a restaurant table? Our habitual response is to pull out a phone and start checking email and social media.
When mobile devices are a distraction from the reality we don’t give them our full attention. While we’re waiting for real-life to resume we’re not scrutinising every email to see if they’re legitimate or not. We’re just browsing and opening things to kill time. In this state of mind, it’s so easy to fall for a phishing attack.
Corporate Protections Do Not Apply
Mobile devices are often treated as personal devices, even if the company provides them. While most corporate laptops and desktops will have enterprise-grade antivirus software, most mobile devices won’t. Nor will they be forced to use the corporate web-filtering software to browse the internet. (For many companies putting those protections in place crosses a privacy line that is uncomfortable to cross for both parties). The device probably won’t even be using the company’s standard mail-client. Yet people will still use them to read their work emails.
The result is a device that has the same level of access to email-based information as the hardened PC sitting under a desk, but without anything to keep that data and the user safe.
Smaller Screens Have Less Detail
In a desktop environment, users are given a lot more to work with when determining if an email is good or bad. Desktop email clients, for example, have a lot more room to display information about who the sender is, what kind of attachment emails include, and where links go when you hover your mouse over them.
Mobile email clients, on the other hand, mask most of this information by default. In the Mobile Outlook app, the only way to view the sender’s email address is to tap on their display name to reveal the full email address.
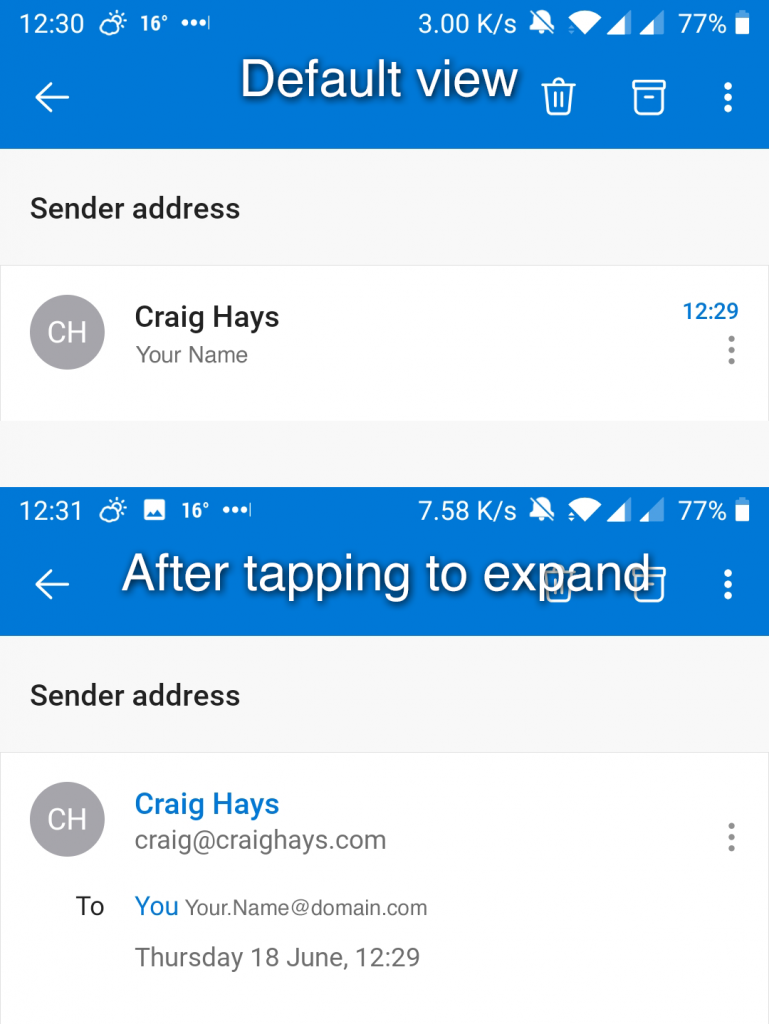
It takes an extra touch input on the sender name to show this information. How often do you do that? Every email? Now and then? Only when you’re not sure? I know I don’t do it for every email I receive. You can hold the text of a link to show the true destination, but how many people know, remember, and use that?
The same applies for web pages once you have clicked on a link in an email. In a browser, it’s easy to see the full URL of the page you’re on. On a mobile device, the smaller screen masks most of the URL. Only a fraction of what can be seen on the desktop is visible. In order to see the full URL, you need to tap on the address bar and do that weird dragging-the-cursor-through-the-text thing to get from one end to the other. The harder it is for people to do something, the less likely they are to do it.
Timing Is More Important
The best time to send phishing emails is when people are reading them. Early in the morning, between 7 am and 9 am, people are reading emails on mobile devices while commuting to work. If an email lands in an inbox while the owner is in it they’re much more likely to read and act upon it. The longer an email sits in an inbox, the less likely it is to be opened.
Not only are they distracted because they’re commuting, but they also have no choice but to use a device with fewer protections and less information to make informed decisions. When an effective phishing email lands while someone is commuting, it will be seen, it will probably be read, and there’s a higher probability that it will be acted upon.
So What Can We Do About Phishing on Mobile Devices?
Regardless of the fact that mobile phishing is a significant risk, our response should be the same as for all phishing attacks.
Multi-Factor Authentication (MFA)
First of all, assume it’s going to happen eventually. Make sure Multi-Factor Authentication is enabled and enforced for all accounts. Even if anyone gets phished, it’s harder for criminals to use stolen credentials as another piece of secret information is needed along with the password that was stolen. While it is possible to phish an MFA login, it’s much harder. The extra effort required is often enough to divert the attention of criminals elsewhere.
Add Warning Banners to External Emails
Since people are reading emails, add a warning banner at the top of all emails that come from outside your organisation. Make them big and unmissable. There’s no point in having something small and insubstantial. It has to literally be ‘in your face’ when you open a message.
Change them regularly – once every week or two. It doesn’t take long for them to become the norm and blend in with the rest of the noise. Before you know it people will instinctively scroll straight past ‘that message’ without reading or acknowledging it.
Educate and Inform
Use phishing simulation tests to send people fake phishing emails and monitor who opens them, clicks the links, and leaks data to them. Each time someone fails the test, use it as an opportunity to provide targeted anti-phishing training. When someone correctly reports a phishing email, give them positive confirmation that their behaviour was correct. The most important part is the training, not the testing (and certainly not penalising those who fail).
Use targeted training sessions to educate and inform people on the dangers of phishing attacks, what they look like, what they’re trying to achieve, and why. Follow up with targeted phishing tests to approximate the effectiveness of your training. But remember, people will always fail in the long run. The right phishing email at the wrong time will catch every one of us out in the end.
Leave a Reply