Free and open proxy servers promise anonymous internet access, but at what cost?

In a world of ever-decreasing online privacy, it’s easy to get sucked into the ‘use an anonymous proxy to stay safe’ narrative. I’ve got nothing against using reputable proxy services or VPNs (virtual private networks), but the ‘free’ proxy services you find on the web can be anything but.
What’s the Difference Between a Proxy and a VPN?
People use proxies and VPNs (Virtual Private Networks) to hide their real IP address and masquerade as other devices on the internet. There are many reasons to do this including bypassing content geo-restrictions, bypassing government filters (Great Firewall of China), bypassing censorship enforced by your Internet Service Provider (ISP), and hiding your real identity from others online.
Your standard internet connection gives you direct access to everything on the internet. Web pages, Skype and Zoom calls, online gaming, it all goes straight from your device to the final destination. To everyone else on the internet, you are you. Your access is limited to what your ISP and government will let you see. All of your traffic is from the country in which you reside.
A virtual private network (VPN) wraps all of your online activity in an encrypted envelope and sends it to another server, your VPN server. This server then unwraps it and sends it to where you wanted it to go. To everyone else on the internet, you are the VPN server, not the real you. Depending on the location of your VPN server, you will be able to bypass some or all of the restrictions described earlier.
A web proxy receives requests for web pages from your device and fetches those pages on your behalf. All other communication remains direct from your device to the destination servers and back. To all web servers on the internet, you are the proxy server. To everything else, you are you. This has a similar effect to a VPN but only for web browsing.
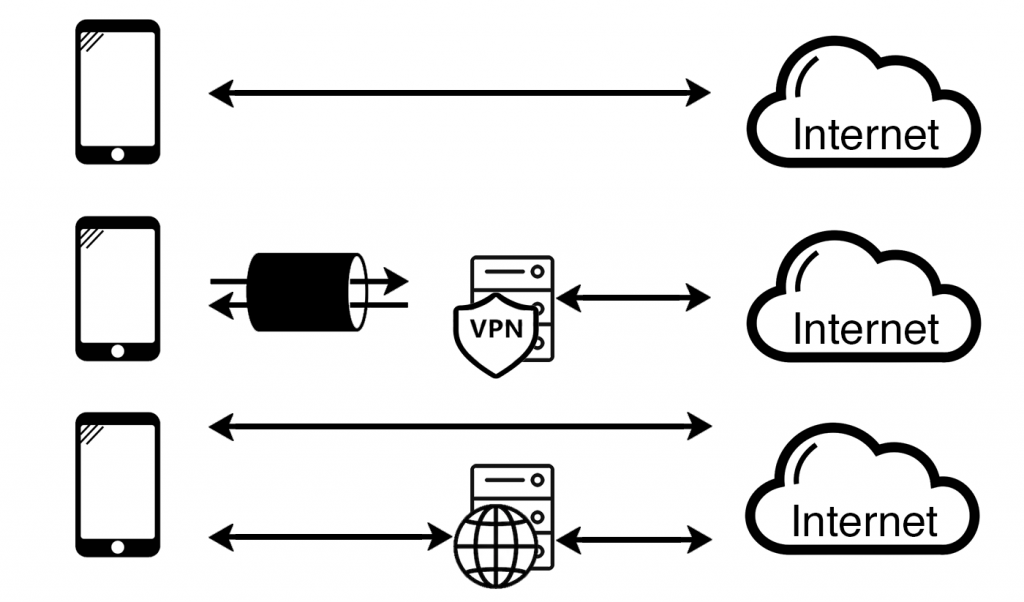
In summary, a VPN moves your visible internet connection from your device to a remote server. A proxy server fetches web content on your behalf but you still appear as your device to anything non-web related.
Free vs. Paid Proxies and VPNs
When you pay for a VPN or web proxy you can expect a minimum level of service in exchange for your money. That minimum level covers things like:
- High-availability of access
- Good transfer speeds
- Untampered data transfers
- No logs stored anywhere of what you do (optional for anonymous VPNs/Proxies)
They make money because you pay them. Therefore, they are incentivised to give a good service to keep you coming back for more.
Free VPNs and proxies, on the other hand, don’t make money directly from you. Sure, some of these services offer a ‘free tier’ where they give you a few GB of transfer for free each month. They make a profit when you upgrade to the paid version. These are freemium services with limited trials that entice you to upgrade and pay. When I talk about free proxies and VPNs I don’t mean limited-use free trials.
A ‘free’ service is one that never asks you for money, ever. When you look at these services, you must ask yourself, “why do these exist?” People generally don’t run free VPNs and open proxies for the good of humanity. When you consume these services they’re likely to be using you in some way.
As the saying goes, “if you’re not the customer, you’re the product.”
Finding ‘Free’ Open Web Proxies
A quick search on google for ‘open web proxies’ or ‘anonymous web proxies’ returns thousands of results with links to websites listing proxy servers that anyone can use without paying a penny.
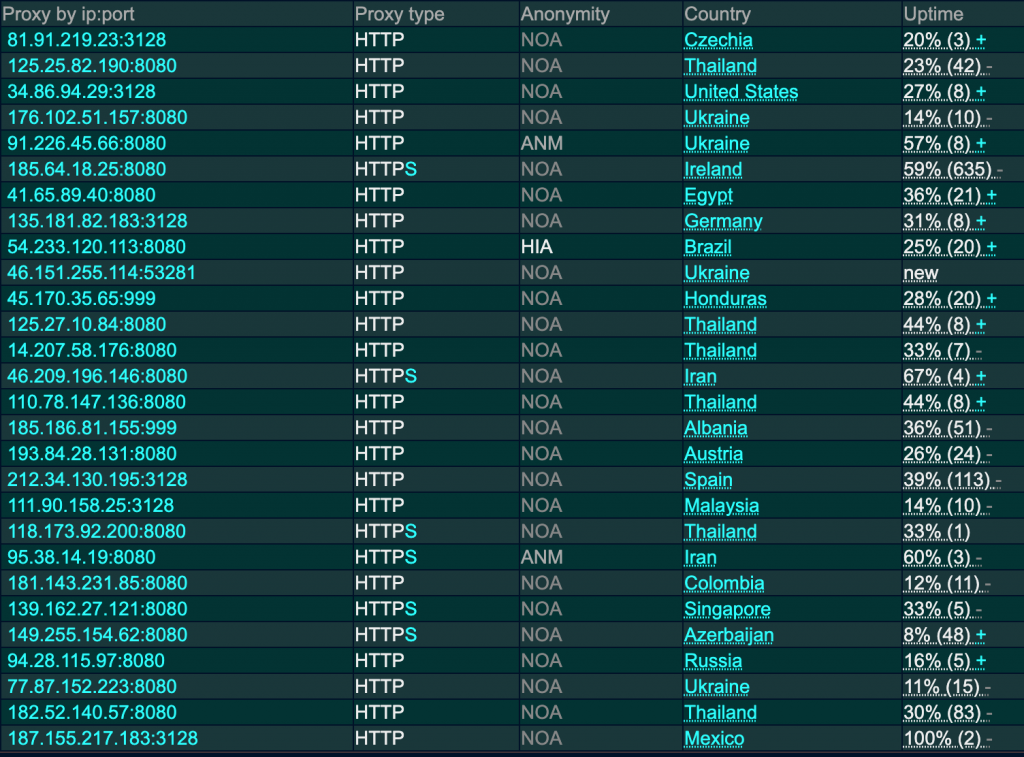
The above is a screenshot of one of these lists. Each list contains lots of server IP addresses and ports. Anyone can configure their web browser to use any of these free, open proxies to proxy all of their web traffic to the internet. None of these servers come with any guarantees and there’s no indication of who is operating them. Many of them are in countries with very lax cybersecurity laws.
Proxy directories maintain their lists by brute-force scanning the internet for open proxies and accepting user submissions by random members of the public. There is no quality control, no peer review capability, and no oversight in any way. This means people like me can set up our own malicious ‘anonymous’ proxy servers and, within a few minutes, have strangers on the internet sending us all sorts of things.
So what can we do to the users of open proxies?
Data Loss Through an Open Proxy
If you use a proxy server for browsing the web, anything you send or receive that isn’t encrypted, (anything in plain text), can be read by the owner of the proxy service. When your communications are encrypted, the attacker can spoof messages from the target server and force you to downgrade your encryption to a crackable level. When this happens, the server can crack the encryption and read your messages without you ever knowing about it. You or your company IT team can configure your devices to prevent this, but how many actually do it?
Failing that, any content you download that isn’t encrypted can be altered to change all links to secure HTTPS sites to the insecure, plain-text HTTP version. You may not even notice that your browser is no longer asking for encrypted versions of sites as it usually would.
This probably isn’t something you need to worry about with a legitimate service, but that ransom, open proxy server you found on the internet?…
Data Tempering and Content Injection by the Proxy
When data is unencrypted (plain-text), malicious proxies can do more than read what you’re talking about. They can actively contribute to the conversation.
Imagine what would happen if you received a quote for a service and the proxy server you were browsing through changed the bank details of the intended recipient to their own? What if they blocked your content altogether? What if they corrupted it so that it couldn’t be trusted? All of these things are possible when you’re using an untrusted machine-in-the-middle of your comms.
Something else which is possible is ad-fraud. The proxy owner changes any advertising content requests sent by your browser for their own ads. The subtlety of this may vary and you may not even notice it happening. When it does, the legitimate owner of a site loses the revenue you would have generated for them. For many site owners, advertising revenue is what keeps them online.
One of the scariest things I’ve seen with open proxies is the injection of malicious javascript code into the existing javascript of every web page downloaded. Nothing else was changed, it just loaded a small piece of code into your browser every time you opened a new page. This code can access your cookies, make requests on your behalf, and even join a botnet directly from your browser.
Hanging Around With a Bad Crowd
Something not often discussed with open proxies is the behaviour of other users. While you might not be committing any crimes via an open proxy, that doesn’t stop others from doing it beside you. If someone commits a crime and the ‘anonymous’ proxy server is confiscated and reveals its not-so-deleted logs, your IP address and traffic history is going to be right there with the criminals. For pretty much every scenario I can think of, I wouldn’t want my name and address linked with that activity.
Summary
Open proxies may look like a good deal, but most of the time, they’re not. If you’re not paying for them you’re most likely to be the product being sold. Stick with paid and legitimate services to stay safe. The prices are relatively low and the ‘free’ versions could cost you more in other ways.