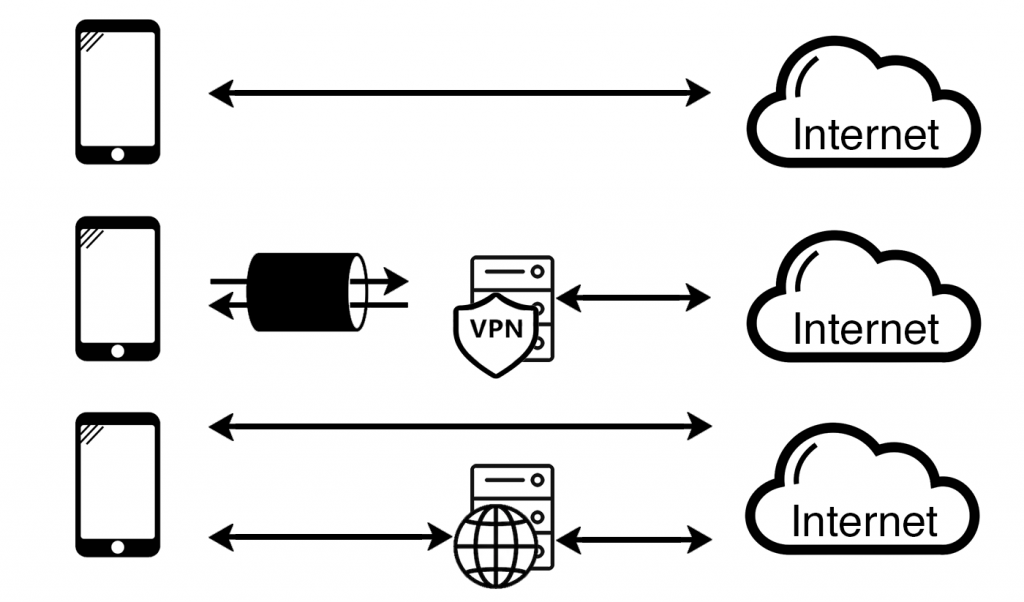
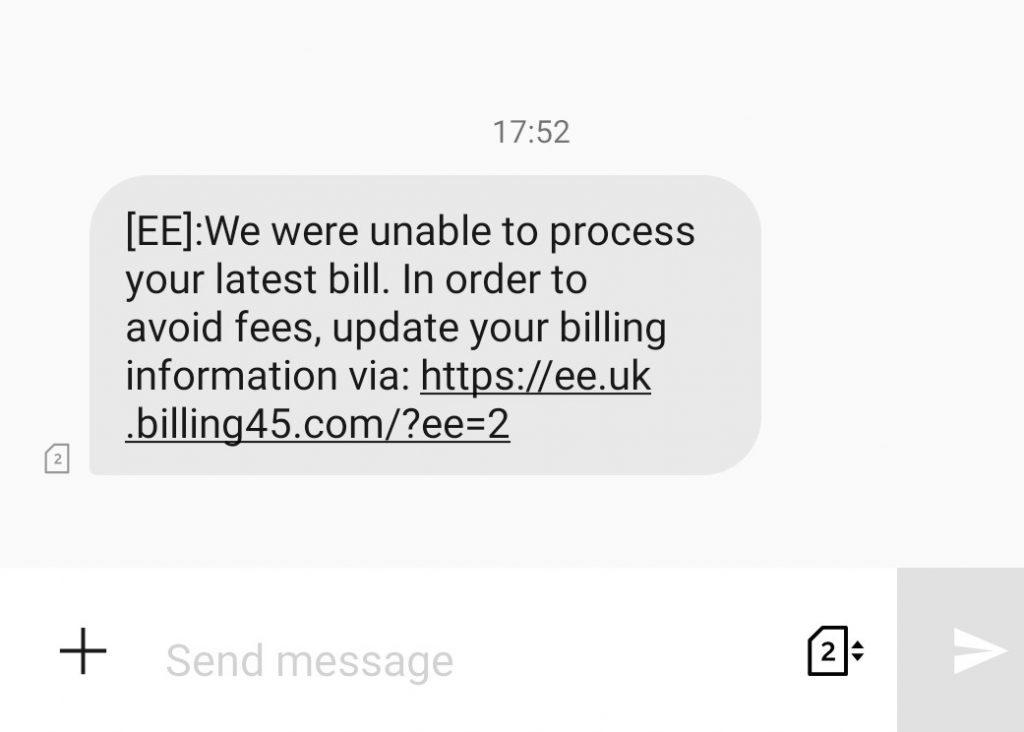
Intro paragraph
Cybersecurity Transformation – Level 1
Setup
☐ Get buy-in from the top
☐ Assemble cybersecurity team
Asset Management
☐ Create an asset register
☐ All devices owned or used by the organisation
☐ All identity providers used across the organisation
☐ All user accounts and their levels of privilege
☐ All IP addresses in use by the organisation
☐ Internal IPs and ranges
☐ External IPs and ranges
☐ All DNS records managed by the organisation
☐ Internal DNS
☐ External DNS
☐ All data owned by the organisation
☐ Identify which data is personal
☐ Identify which data is commercially/operationally sensitive
☐ Identify which data is public/non-sensitive
☐ Create a service catalogue for all services/systems used by the organisation
☐ Define the criticality of each service/system based on it’s importance to the primary objectives of the organisation
☐ Things you can’t live without for more than a few minutes – mission-critical
☐ Things you can’t live without for more than a day – mission-support
☐ Things you can live without for weeks or months at a time – administrative
☐ Define a security classification for each system/service based on the impact of:
☐ Loss of Confidentiality of its data
☐ Loss of Integrity of its data
☐ Loss of Availability of its data
☐ Map all components of each service/system to define a complete list of:
☐ All servers that make up the service/system
☐ All identity providers that provide authentication
☐ All user accounts that can access the system and their level of privilege
☐ All IP addresses used by the service/system
☐ All DNS records related to the service/system
☐ All data stored or processed by the service/system
☐ All of the above split down by operating environment: e.g. Production, DR, Test, Development, etc.
Hardening the Network Perimeter
☐ Setup vulnerability scanner(s) on external network
☐ Setup vulnerability scanner(s) on internal networks
☐ Implement a process to continuously update the asset register based on output from vulnerability scanner asset discovery
☐ Block access to anything visible from the internet that isn’t required for the primary objectives of the organisation
☐ Admin portals
☐ Remote administration tools
☐ Configuration pages
☐ Internal-only stuff
☐ Unused ports
☐ Unused IP addresses
☐ Used ports that aren’t used by genuine end-users of the service/system e.g. only allow TCP ports 80 and 443 on web servers and block everything else
☐ Enforce Multi-Factor Authentication for all authentications from the internet
☐ Staff VPNs
☐ Admin VPNs
☐ Internal/third-party remote support access (VPN, Citrix, Azure Virtual Desktop, etc.)
☐ Cloud-delivered services e.g. Office 365, Azure portal, Google Workspace, etc.
☐ On-premises applications exposed to the internet
☐ Enforce secure Multi-Factor Authentication registration by requiring MFA or trusted IP address (fixed organisation external IP) or one-time token created during the ‘new user’ onboarding process
☐ Fully patch everything visible from things on the internet
☐ Implement a process to patch everything visible from the internet, every day
Hardening Identities
For each identity provider (including in-system identity providers):
☐ Disable unused user accounts (not logged in for 60 days)
☐ Disable unused device accounts (not logged in for 60 days)
☐ Disable unused service accounts (not logged in for 60 days)
☐ Delete unused user accounts (not logged in for 90 days)
☐ Delete unused device accounts (not logged in for 90 days)
☐ Delete unused service accounts (not logged in for 90 days)
☐ Identify user accounts shared across multiple people
☐ Migrate shared user accounts to single users and delete shared accounts
☐ Add an EmployeeID field for all user accounts and populate it with the account owner’s Employee ID from your HR system
☐ Identify any users not registered/configured for MFA and block their access from the internet (untrusted IP addresses) if services using the identity provider can be accessed from the internet
☐ Setup a banned password/passphrase dictionary that prevents password changes where 60% or more of the password is found in common password lists or words or phrases related to your organisation, its locations, its products, seasons, months of the year, days of the week, years in numerical format, anything like changeme, welcome, etc.
☐ Identify critical service / autologin / terminal device user accounts that are used on more than one computer at a time (e.g. POS machines)
☐ Migrate critical service / autologin / terminal device user accounts to one account per device (this reduces the impact when you need to force a password change in future)
☐ Create and execute a process daily to identify anyone who has left the organisation and disable and delete their user accounts from every identity provider by linking it through the EmployeeID field
☐ Setup a robust joiners, movers, and leavers process to reduce the number of exceptions identified by the daily cleanup process
Privileged Access Management
For all Windows end-user devices (PCs. Laptops, Surface Tablets, etc.):
☐ Setup LAPS to manage the built-in administrator password
☐ Remove all other users from the local administrators group – document any exceptions for later
☐ Implement Role Based Access Control for accessing LAPS managed passwords
☐ Enforce MFA before anyone can view LAPS managed passwords
☐ Enforce a rate limit for the number of LAPS managed passwords a person can view in an hour/day
Secure Your Infrastructure
☐ Implement and enforce a secure DNS resolver service to automatically block bad stuff
☐ Block all outbound traffic to the internet by default and only permit specific types of traffic (web browsing, voice, etc.) to specific locations wherever possible
☐ Domain/organisation network edges
☐ Host-based firewall on end-user devices (public/guest/private networks)
☐ Host-based firewall on end-user devices (domain/organisation networks)
☐ Implement a web security gateway with HTTPS decryption for all end-user web browsing and block:
☐ All uncategorised websites
☐ All newly registered websites
☐ All known malicious/harmful websites
☐ All lookalike domain websites
☐ All websites with categories that have no business or limited personal use purpose within your organisation (gambling, pornography, hate, self-harm, etc.)
☐ All web traffic trying to bypass the secure web gateway unless it’s an approved direct-access service such as Office365, Zoom, Google Workspace, etc.
☐ Block removable storage devices – document all per-user exceptions for later
☐ Fully patch all internal device operating systems
☐ Fully patch all internal device application runtime frameworks (.NET, Java, etc.)
☐ Fully patch all internal device applications
☐ Define SLAs for routine patching. E.g. Critical in 24 hours, everything else within 30 days of release
☐ Implement a regular patching process to patch all vulnerabilities within SLA
☐ Implement a process to discover all software installed on all devices and update at least daily
☐ Remove all software from all devices that isn’t required
☐ Create a software inventory/catalogue of all remaining, authorised software
☐ Review license requirements of all software in the software catalogue for license requirements
☐ Aquire licenses for any shortfalls / remove unlicensed software from the environment
Protect Email Users
☐ Implement SPF and DKIM protection policies to drop spoofed and tampered emails
☐ Block spam/bulk mail
☐ Implement attachment sandbox execution and malware/phishing detection
☐ Implement link sandbox execution and malware/phishing detection
Cybersecurity Transformation – Level 2
Privileged Access Management
For all Windows end-user devices (PCs. Laptops, Surface Tablets, etc.):
☐ Implement Restricted Groups or similar tools to prevent unauthorised users from being added to local administrators, remote desktop users, etc.
Protect Email Users
☐ Implement and enforce DMARC protection on all inbound email from outside your organisation
☐ Implement browser isolation sandboxing on all links in inbound email from outside your organisation – document exceptions from trusted senders
☐
☐
☐
☐
☐
☐
☐
☐
☐
☐
☐
☐