SMS based phishing attacks (Smishing) are a real threat that we see every day. To help you spot them in future, this is how they work.
A Phishing/Smishing Attack In Action
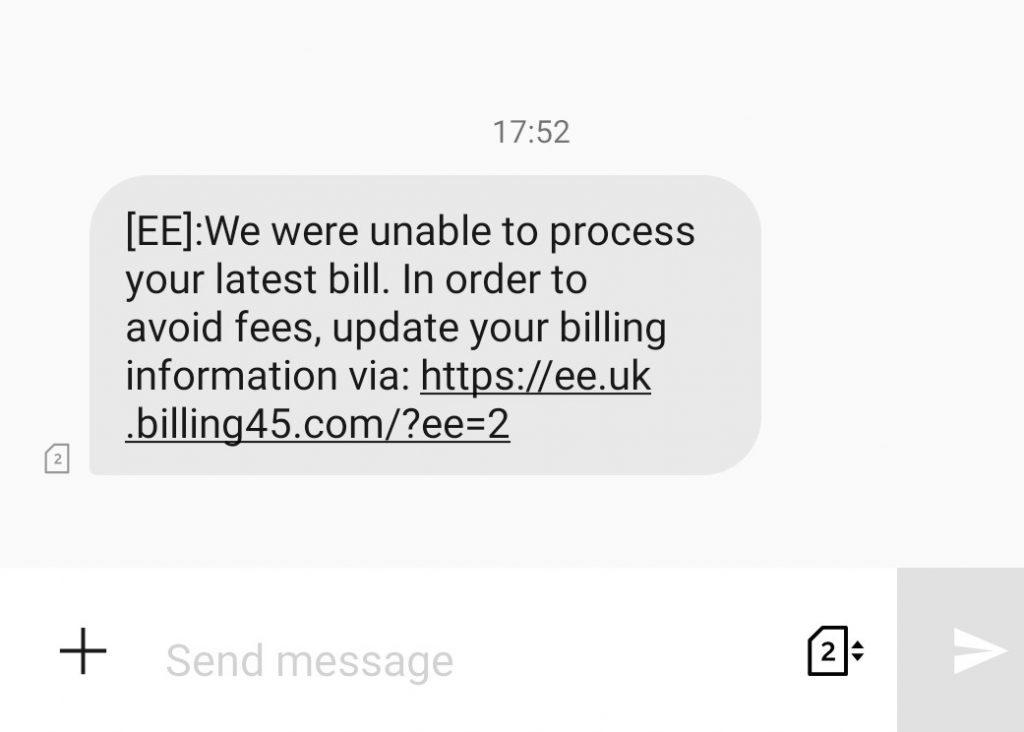
At 17:52 pm today I received a text message from my mobile phone network, ‘EE’. I picked up the message at 18:08. This is what it said:
[EE]:We were unable to process your latest bill. In order to avoid fees, update your billing information via: https://ee.uk.billing45.com/?ee=2
It’s not a real link. I’ve made it unclickable. Please don’t visit it…
So that’s weird. Yes, I’m an EE customer and they send me text messages all the time. But that domain looks strange. Let’s check it out. What happens when I visit the link with Chrome on my Android phone?
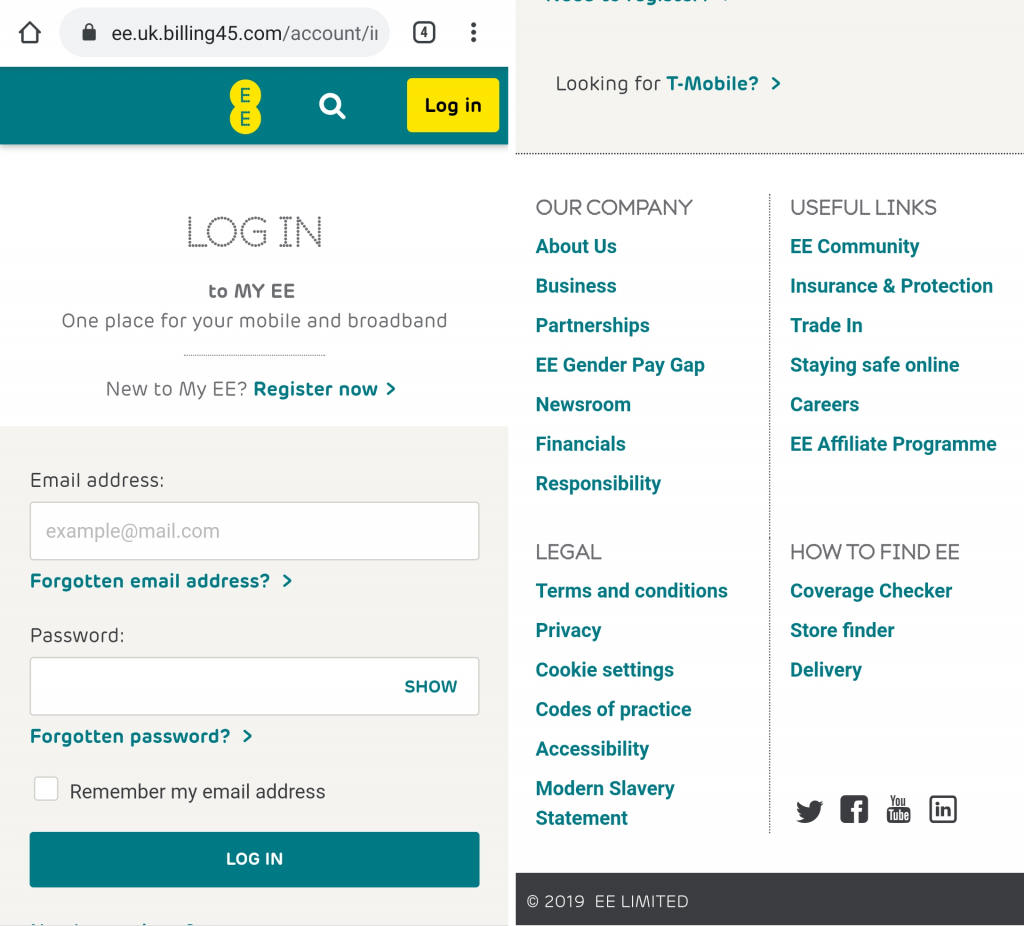
It works! And it looks pretty real. That’s almost exactly what I see whenever I visit the EE site on my Android phone. However, four things stand out immediately:
- The domain is not a domain I trust. I’ve no idea who billing45.com are.
- The copyright statement is 2019. It’s over a month into 2020 now. Either EE generates this value dynamically or someone will have updated it by now.
- Most of the links in the footer do nothing. Some of them actually take you to real EE sites. The link to newsroom actually works…
- It’s got the secure padlock we’ve all been trained to look for. Looks legit, right? Maybe not.
When I open the site on my laptop however, Chrome gives me a big red warning message:
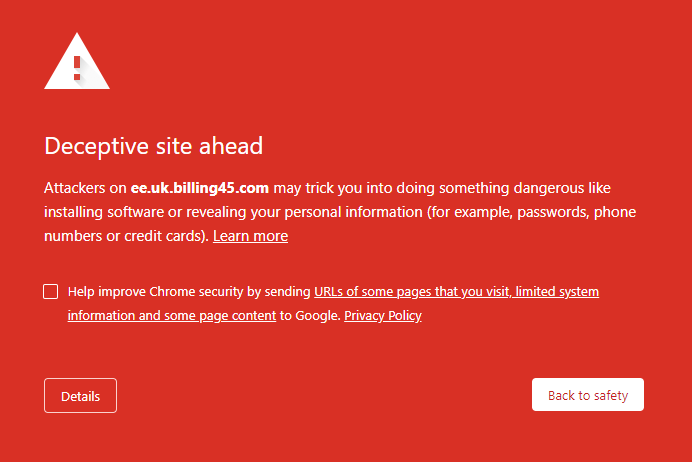
What concerns me here is that I use Chrome on both my Android smartphone and my laptop and yet mobile Chrome did nothing to protect me. @Google, why do you protect desktop users but not mobile?
Undeterred, I proceed to update my billing details because I don’t want my phone to be cut off and I can’t afford to pay any late fees. I immediately and successfully login with a made-up username and password. Had I chosen to register as a new customer I’m sure that would have worked too.
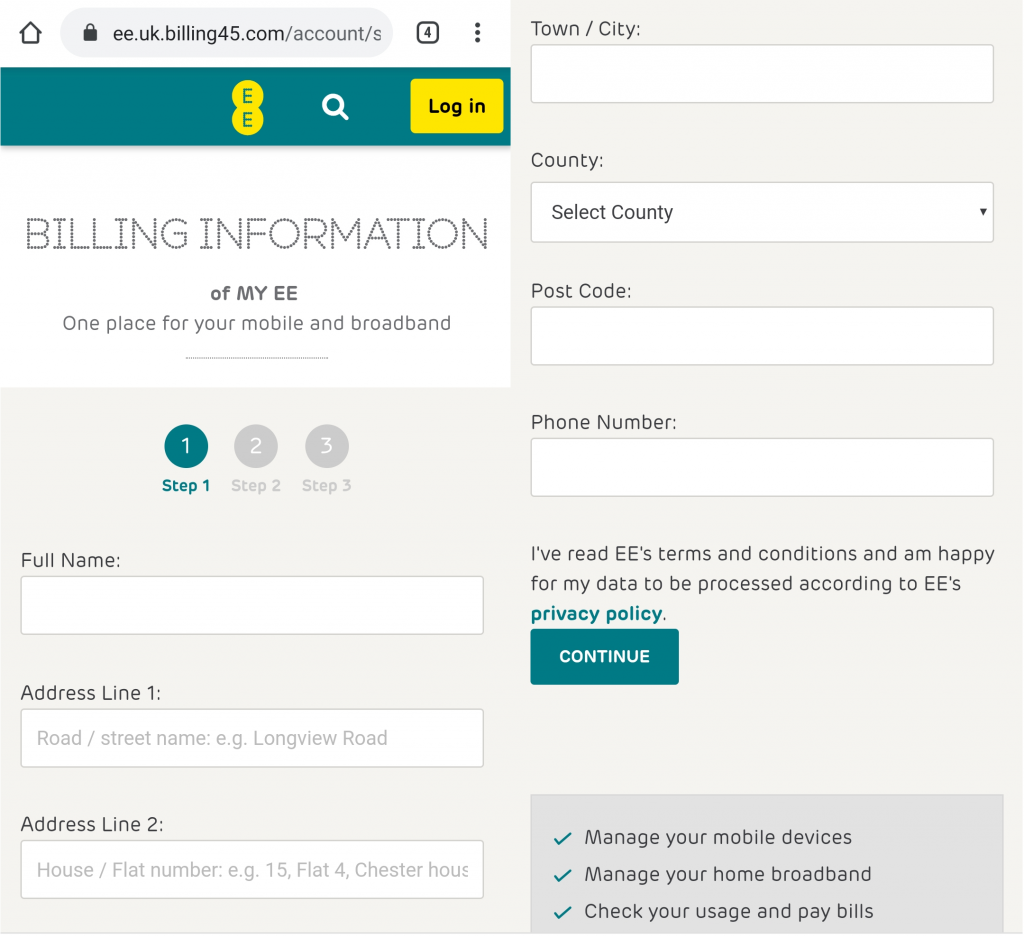
Now that I’m logged in I can update my billing information. Except, the top right of the page is still asking me to ‘Log in’… I thought I just did that…
Anyway, all of these things look like perfectly reasonable pieces of information to ask for. I complete the form with more made-up details. Fortunately, I didn’t get any of those annoying, red, data validation errors on any of the input fields! How refreshing. Onwards to the next page.
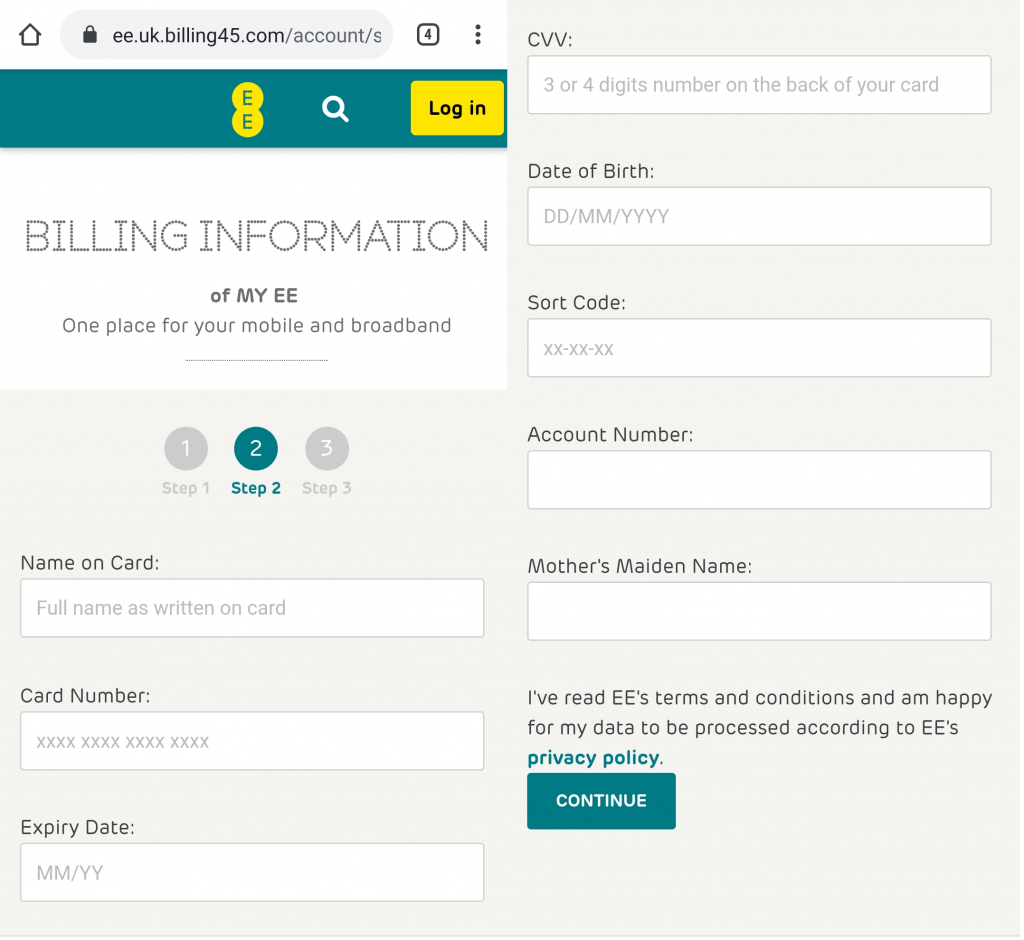
OK. This page looks a little bit more suspicious. The look and feel is just like the real EE site but now they want my full name as shown ‘on card’, (whatever card that might be), card number, expiry date, the CVV code from the back/front of my card of choice, my date of birth… my sort code for my bank account, my bank account number… and my Mother’s Maiden name. All of those things look totally normal and definitely go together on a single page like this one, which still wants me to ‘Log in’.
Still undeterred, I invent all of those details and move on to the next page.
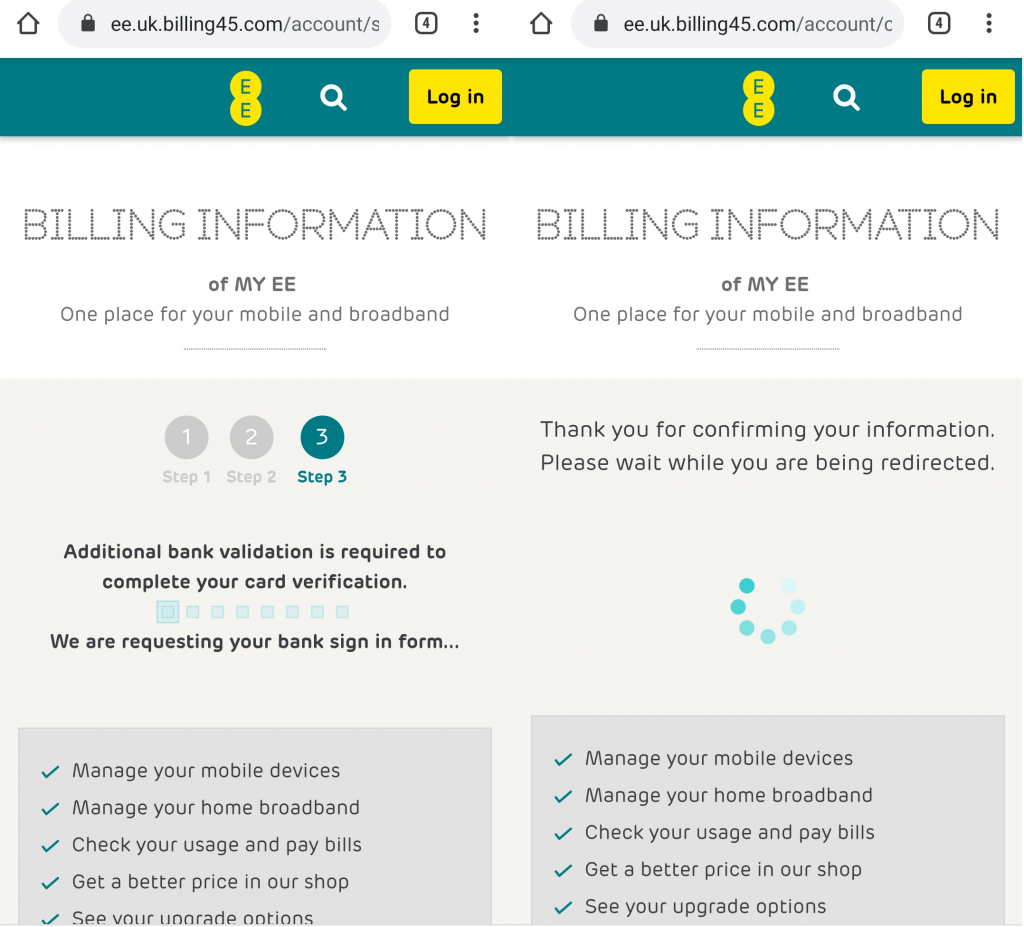
Excellent, I see the bank validation lefty-righty flashy-lighty page that the bank always does when validating stuff. Then the site presents me with the swirly-whirly ‘redirecting you’ page. Everything is looking good! My fingers are crossed and I’m hoping that everything worked.

It Worked! I’ve successfully updated my name, address, date of birth, payment card details, bank account details, mothers maiden name, and inside leg measurement. Now I’m back on the real EE website and ready to log in to win huge tech prizes.
And I’ve just been phished. Easy as that.
Digging Deeper Into the Phish
Now that we’ve seen what it does, let’s dig into the details a bit further.
The Phishing Site URL
I expect that the link in the text message would look pretty convincing to most people: https://ee.uk.billing45.com/?ee=2. How are we to know it isn’t legit? It even has https to show us that it is a ‘secure website’. More on that later.
The end of the URL has a basic form of authentication included. The ee=2 parameter causes the page to load successfully. If you take away the ee parameter or change the value 2 to any other value the page fails to load.
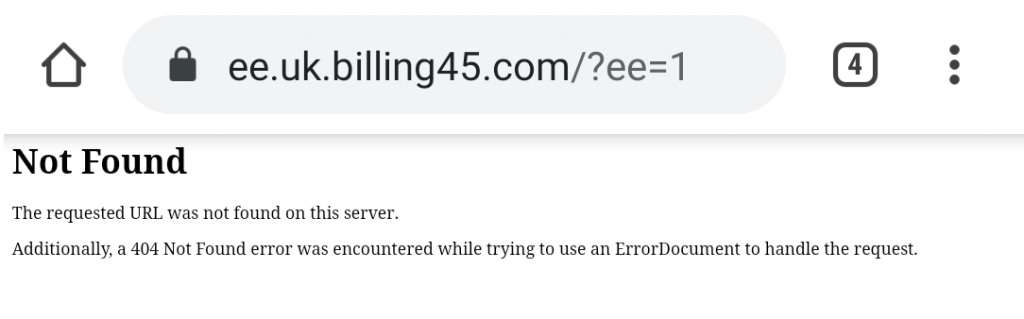
This is a security/stealth mechanism to prevent people from stumbling upon the page by accident and reporting it. Automated web crawlers index good content and bad. The data captured can be used to identify phishing pages in the wild. By needing a token to access the phishing page (ee=2), automated crawlers are much less likely to stumble upon the site.
Phishing Site Software
Phishing sites are usually deployed using pre-built phishing kits. People write phishing kits for targeting different types of applications, websites, and people, and sell them to criminals who then deploy and use them as they see fit. The kits make it easy to deploy a site, capture sensitive information, verify visitors as potential targets through the use of a simple token (ee=2), redirect users to the real site after they’ve been phished, and switch the kit on and off.
This phishing kit is written in PHP and seems to only target the EE brand. I haven’t spent a lot of time trying to brute force other brand names to see if they also exist but I think it is unlikely. The URL in use is tailored to the EE brand to match the phishing kit content. There may be other phishing URLs hosted on this server but I haven’t gone looking for them.
The Padlock Is Dead
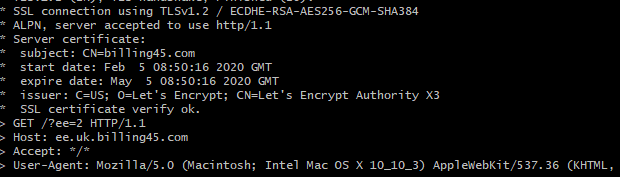
The https padlock on this site simply shows that traffic between your browser and the webserver is encrypted. Nothing more. The SSL encryption certificate which your browser uses to verify the site is indeed ee.uk.billing45.com is provided by https://letsencrypt.org/. This is an excellent service as it allows anyone to encrypt traffic to and from their website for free. Sadly, that also includes the bad guys who want a padlock on their malicious websites. Letsencrypt is great for privacy but not so great for preventing phishing attacks.
To display a padlock on this site, all the admin needed to do was request and approve a certificate through the LetsEncrypt platform. They’re generated in a few seconds and installed automatically. Once done, the site is trusted by all modern browsers. The visible padlock gives the site credibility despite the fact that no credibility checks have actually been done.
We spent years educating people to only trust web sites with the padlock in the URL bar. Today, anyone can get a padlock with almost no upfront cost or effort. The ‘trust the padlock’ message is now working against us.
Writing Phishing/Smishing Text Messages
In my article 9 Things I’ve Learned Writing Phishing Emails I talk about the use of language to convince people to take a specific action. The words ‘in order to avoid fees’ are all that is needed to convince many people to click the link and start filling in details. Our aversion to loss, paying more money than we should have done, is a very strong motivator.
SMS messages are capped at 160 characters of text including spaces. Because of this, a phishing message delivered over text message needs to be short, specific, and powerful. Every character is precious. This smishing message achieves:
- Authority. ‘[EE]’ identifies them as the phone provider, EE. If you receive this message and EE is indeed your phone provider then they’re stating that they have power over your contract and your connection to the rest of the world.
- Define a problem. ‘We were unable to process your latest bill.’
- Invoke feelings of fear, loss aversion, and urgency. ‘In order to avoid fees’. The urgency is an implicit statement as we all know that late fees are a very real thing.
- The solution to your problem. ‘Update your billing information via…’ tells you how to prevent feeling the pain alluded to in 2 and 3.
Phishing Sites are Monitored in Real-Time
These sites are monitored while SMS phishing attacks are taking place. SMS messages are sent at a cost and attackers want to make the most out of their investment. Sending 10,000 text messages and watching for responses for the next 2 hours will yield an excellent return on the black market. It also allows attackers to spot threats and shut their operation down when people like me start poking around.
In order to walk through this phishing experience, I entered false details on every page. At the end of the process, all of the information will have either been written to a local file on the server, sent to a remote server, or emailed to a free email address from Gmail, Hotmail, Protonmail, etc.
By the time I went back for a second pass at 18:16, just 3 minutes after I submitted the forms, someone had seen my fake details and deactivated the phishing kit. If you visit /?ee=1 or any other non-verified link you still get the same error message as before. If you visit /?ee=2 you get redirected to the real EE.co.uk website instead of being shown the phishing kits data capture pages.
I suspect that my clearly made-up information alerted the attacker to the fact that I’d discovered their scam and that their time was up. Deactivating the phishing kit prevents further investigation into what the kit does and buys them time to process what they’ve captured so far. Ultimately, phishing attacks are all about stealth. When the game is up, it’s time to move on.
The Impact of Falling for This Phishing / Smishing Attack
If you fall for an attack like this, you’ve given away your email address and password, name, address, and telephone number, date of birth, credit card information, bank information, and answer to a very common security question (mother’s maiden name). All of this can be sold on the black market for profit or used directly to commit fraud, gain access to your other accounts, steal your mobile phone number by moving it from your SIM card to theirs, and more.
Even if you only complete the first of several steps, any information you’ve typed into the forms on your browser should be considered compromised. There’s nothing stopping them from recording each page individually as you move through the phishing site, or even scraping every keystroke you make while on their page, even if you don’t actually hit submit. Once you’re on a phishing site you’re in danger and everything you do is being watched.
If you do fall for a scam like this, change all of your passwords, change all of your security questions, enable Multi-Factor Authentication on all of your accounts that support it, contact your bank, and contact the relevant authorities for reporting cybercrime and fraud.
Phishing is deceptive, to say the least, and it’s easy to see why so many people fall for it. I think that a level of care must come into place, especially if family members don’t typically use email for communication. Pinpointing any discrepancies in language, as you said, goes a long way.