User accounts are still the number one target for criminals. This is why they are so desirable and how hackers hack user accounts every day.

When we think of cyber attacks we often think of scenes resembling those from Hollywood movies. Cybercriminals, slouched over a keyboard, furiously typing, and hunting for vulnerabilities in a piece of software exposed to the internet.
Security vendors leverage this perception in their marketing efforts. I still find it amazing how much fear selling takes place from companies like Tenable, Rapid7, and Qualys, to name a few. Granted, they’re selling software designed to detect known vulnerabilities in other pieces of software, but they exploit the common perception that the sky is falling and that hackers are seconds away from compromising your IT systems.
In reality, most of the cybercrime committed today is done through legitimate user accounts. Real user accounts belonging to real people which have been taken over by hackers with criminal intent. Why is this the case?
Hacking People is Easy. Hacking Software is Hard
People are vulnerable by design. Human nature makes us susceptible to being hacked in any number of ways.
When we use software and computer systems we typically login using a unique username and password that identifies us, proves that we are who we say we are (authentication), and confirms that we’re permitted to do what we’re asking to do (authorization). When a hacker logs in with our user account they instantly get access to do all of the things we are allowed to do.
Software, on the other hand, can be very difficult to manipulate. Even once you’ve found a vulnerability and created an exploit to gain access to something you shouldn’t, you still need to figure out a way to make it do what you want. This is a very time consuming and expensive process. The question hackers ask themselves all the time is ‘why would I waste all of that effort hacking into a computer system when I could just log in as a legitimate user instead?’
This is why user accounts are such a big target. The right account in the wrong hands can move millions of dollars between banks in a few minutes. Trying to do the same thing with a software exploit could take months or even years and isn’t always possible.
Three Ways Hackers Steal Your User Accounts
1. Guessing Your Password
The first way for hackers to break into one or more of your user accounts is to simply guess your password.
The top 10 passwords for 2019, based on publicly known password breaches, are:
- 123456
- 123456789
- qwerty
- password
- 1234567
- 12345678
- 12345
- iloveyou
- 111111
- 123123
Based on these passwords it is a reasonable assumption to state that most of these have been created on mobile devices. The top 10 passwords has changed over the last decade from common words to common number patterns as the ubiquity of smartphones has steadily increased.
Do you use any of these passwords for any of your accounts? Do you have anything similar?
For anyone not using one of the most commonly used passwords, with a little research into an individual it is easy to guess other password formats that people use. Combinations of the following make up the vast majority of the passwords in use today: names of partners, children, pets, football teams, cities, countries, dates of birth, seasons, years, and colours.
I’ve cracked a lot of passwords in my career and I’ve analyzed 1.4 billion clear-text passwords to improve my understanding of how people think about password creation. With a good enough wordlist, you don’t even need to find a Facebook page to guess most people’s passwords.
2. Finding Your Password In Someone Else’s Data Breach
As mentioned in the previous point, there’s a publicly available list of 1.4 billion usernames and passwords on the internet for anyone to download. That’s just one list out of many out there. Every day, additional websites are hacked and new username and password combinations are leaked to buyers on the black market.
Just as your web browser offers to remember and fill in your passwords for you, there’s a password completing browser extension that criminals can use to makes life easier for them when taking advantage of your stolen passwords.
3. Asking You For Your Password (And You Giving It To Them!)
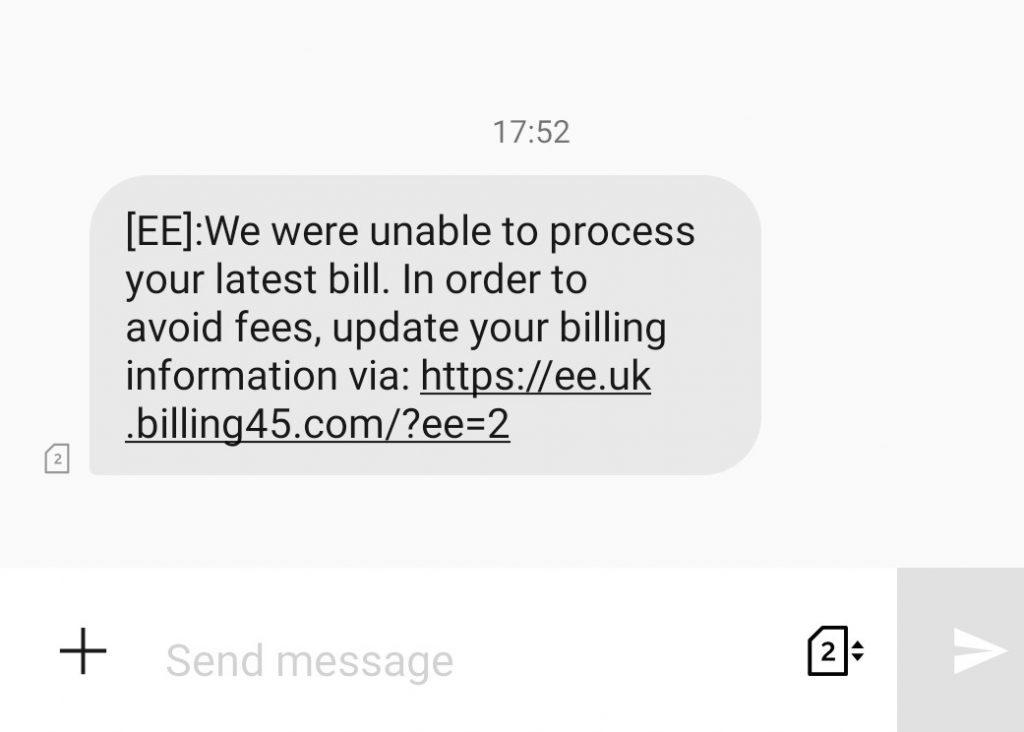
Phishing is an attack where criminals send you an email or SMS text message pretending to be someone else. Typically a company, organisation, friend, or some authority figure that would convince you to do as they say. The message will contain a link to a website asking you to log in, or it could include an attachment. The attachment will then take you to a website, again asking you to log in, or it will run something harmful on your device which could allow it to steal your personal data, including passwords.
Linking to a login form is the most common. It’s surprising how many people still fall for phishing emails today, but phishing emails are often well written and designed specifically to invoke an emotional response in the reader. Emotions overpower logic and reason. People do strange things in a panic.
What Can We Do To Fight Back?
Here are a few things we can do to defend against password theft.
Use Multi-Factor Authentication
Multi-Factor Authentication, or MFA for short, is the use of something in addition to your password to prove that you are who you say you are. In order for multi-factor you need to use a combination of two or more of the following:
- Something you know (your password)
- Something you have (your smartphone)
- Something you are (your fingerprint)
Smartphone apps or SMS text messages are the most commonly used form of the second factor. While it is possible to bypass MFA protected logins that use SMS messages, it takes a lot more effort and involves contacting your mobile phone provider and convincing them that you’ve lost your phone. Without a second authentication factor, as soon as someone has your password, they’re in and your account has been hacked.
Use Strong Passwords
The stronger your password is, the harder it is to guess. Google recommends:
“Long passwords are stronger, so make your password at least 8 characters long. These tips can help you create longer passwords that are easier to remember. Try to use:
- A lyric from a song or poem
- A meaningful quote from a movie or speech
- A passage from a book
- A series of words that are meaningful to you
- An abbreviation: Make a password from the first letter of each word in a sentence”
Use Different Passwords on Every Website
As shown in the 1.4 billion usernames and password list, as soon as one website is hacked, any other accounts on other websites you use with the same username and password are vulnerable to a takeover by a hacker.
We’ve all done it in the past, including me. We pick a handful of memorable passwords and use them across a range of sites. If you ever forget which one you’ve used you can always try them all until you get in. Eventually, it works. This is what hackers do too.
Use a different password on every website. That way, if your password ever gets leaked, it won’t be usable on any other website. As a bonus, if you know which site a password was used on, you’ll know which site’s have been hacked when your passwords do become public.
Use a Password Manager
Let’s be realistic… Having a separate password for every account is unmanageable for most of us. We can’t remember that many unique password combinations. Instead, use a password manager to store unique, strong passwords for all of your accounts.
Modern web browsers have password managers built-in. Companies like 1Password, LastPass, and Dashlane all offer free or paid-for alternatives. There are many options out there and you’re free to choose whichever you prefer. But please, use one and you’ll only need to remember one, very, very strong password to keep all your accounts safe.